Recent News
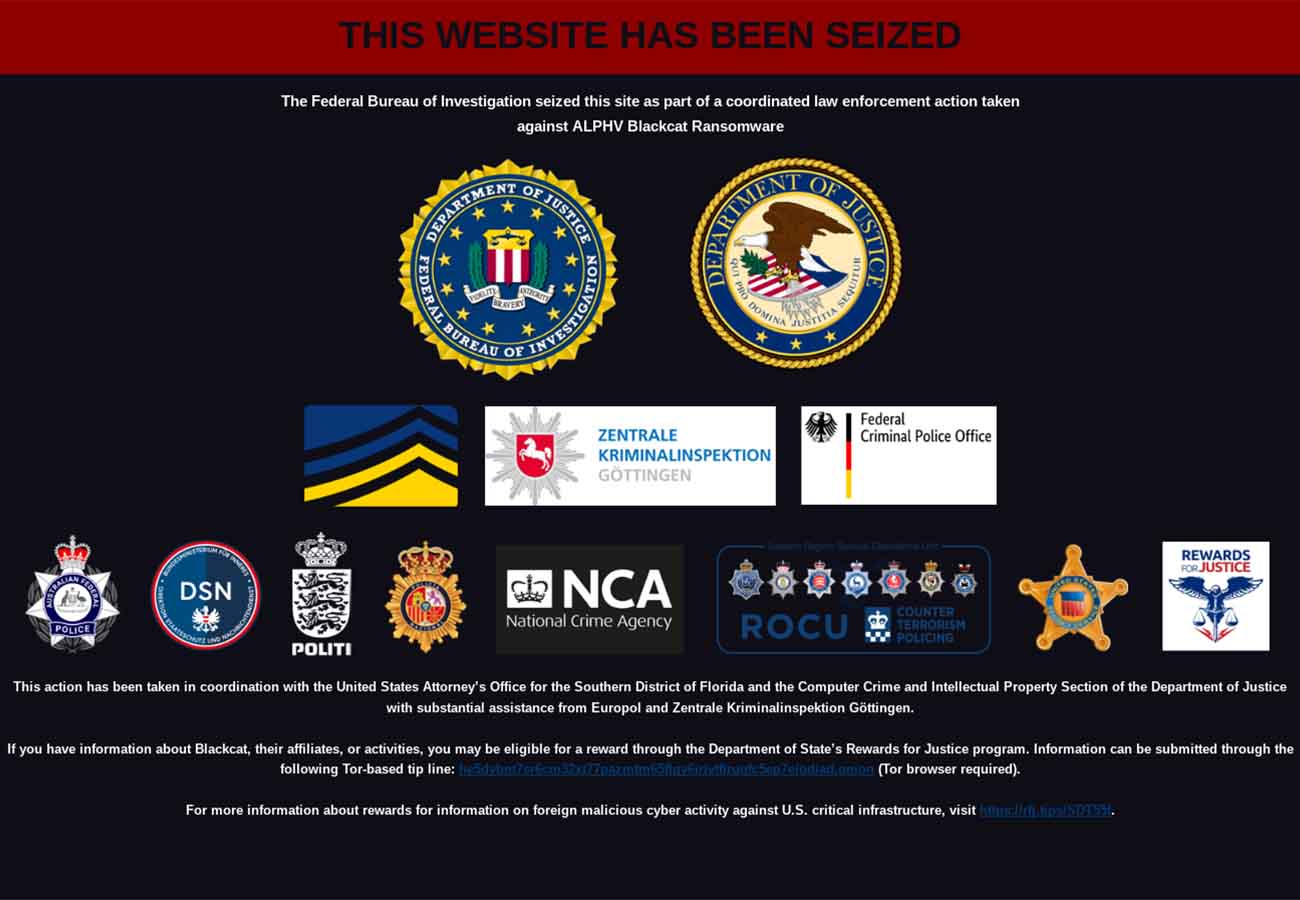
The Second Disruption of ALPHV/BlackCat Operations
 March 14th, 2024
March 14th, 2024
APT29’s Cyber Espionage Evolution: Adapting to Cloud Security Challenges
 February 29th, 2024
February 29th, 2024
Major Brands’ Subdomains Compromised to Send Millions of Malicious Emails
 February 27th, 2024
February 27th, 2024
The Second Disruption of ALPHV/BlackCat Operations
March 14th, 2024
APT29’s Cyber Espionage Evolution: Adapting to Cloud Security Challenges
February 29th, 2024
Major Brands’ Subdomains Compromised to Send Millions of Malicious Emails
February 27th, 2024
Medusa’s Strategic Evolution: Blending Extortion and Stealth in Ransomware Operations
“There are only two types of companies: those that have been hacked, and those that will be.”
— Robert Mueller, FBI Director, 2012
More News
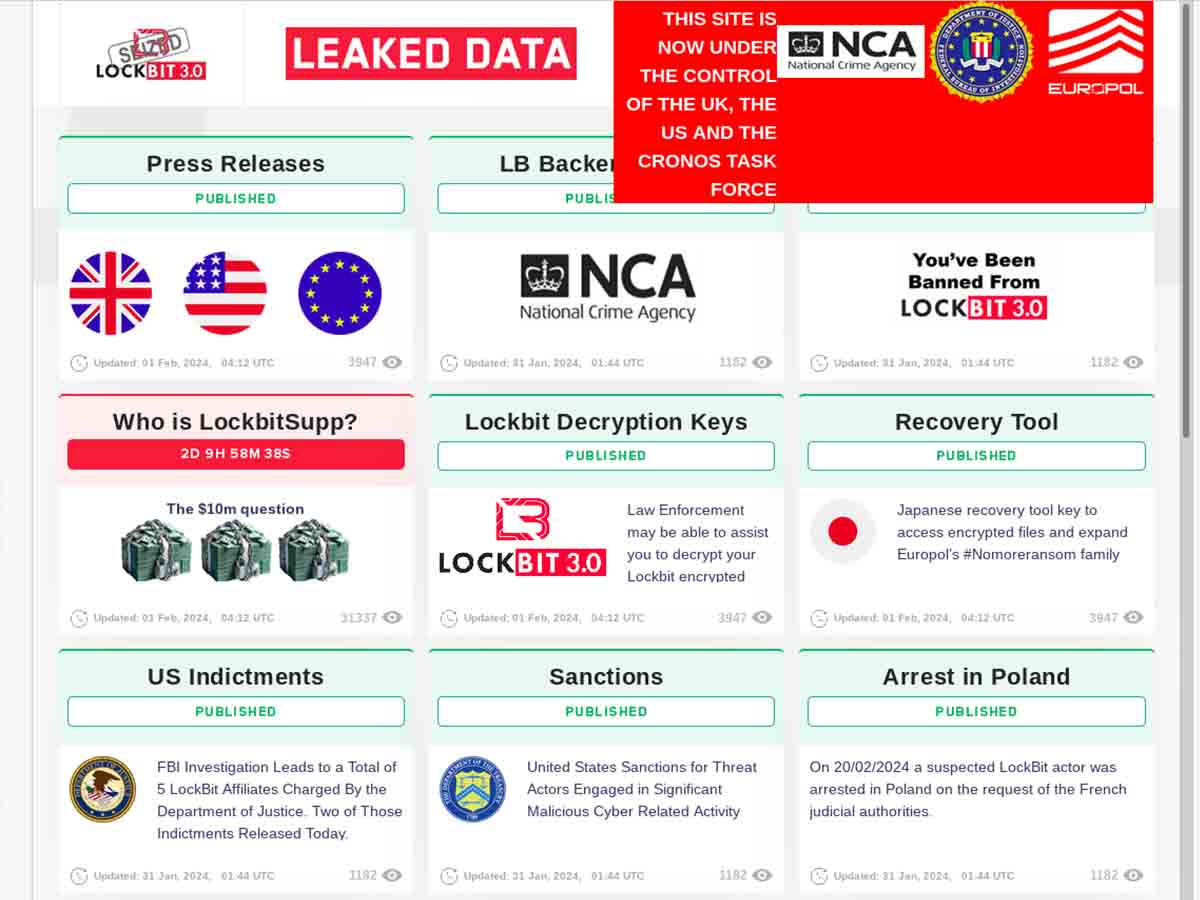
19 Cybercriminals Face Justice in Global Law Enforcement Operation
January 8th, 2024
Sea Turtle Targets Dutch IT and Telecom Sectors
January 7th, 2024
The Admin Behind Cybercriminal BreachForums Was Re-Arrested
January 6th, 2024
Tech Entrepreneur Falls Victim to Cryptocurrency Scam, Loses $125K
January 5th, 2024
Individuals
Richard Stallman: Founder of the Free Software Movement
November 25th, 2023
Zane Lackey: Co-founder of Signal Sciences
November 25th, 2023
Wim Remes: Member of the ISC2 Board of Directors
December 28th, 2023
Whitfield Diffie: Co-inventor of Public Key Cryptography
December 30th, 2023
Knowledge
VirusTotal: The Cybersecurity Practitioner’s Multi-Engine Shield
December 15th, 2023
TCP Fingerprinting: How Reliable Is It?
December 28th, 2023
Trust: How Important Is Trust in Cybersecurity?
December 21st, 2023